How To See If An E-mail Is A Scam
E-mail scams are getting better. But not good enough.
When a new technology comes along, you can be sure that someone will use it to try to scam every gullible idiot they can find. The birth of e-mail was no exception, and e-mail scams are almost as old as e-mail itself.
One of most infamous types of e-mail fraud is perhaps the Nigerian Prince Scam, which is an advanced-fee scam. If you have an e-mail address, there’s a good chance you have been the target of this particular scam. You’ll receive an e-mail from someone claiming that they need your help to access a ridiculous amount of money. To get access to the it, however, the sender needs a little financial aid to bribe some officials, perhaps you can help? For your troubles, you’ll receive a significant part of the money once they have come available to the sender.
Of course there is no money, gold, diamonds, or other valuables, and the money you transfer to the scammers will vanish. I’ve often wanted to reply to one of the Nigerian princes to see how far down the rabbit hole I can go before I have to cough up any money. Maybe one of these days.
In the past, it’s been rather easy to see that an e-mail is not legitimate, but an absurd scam. One of the best pointers is terrible grammar and wording, and weird e-mail layouts. But the scammers are getting better, and a couple of days ago I received an e-mail that looked genuine - at least at first sight. But when I started looking at the details, it quickly became obvious that it was not.
Let’s take a deeper dive into this particular e-mail to see what we can look for to distinguish scams from legitimate e-mails.
You Have Mail
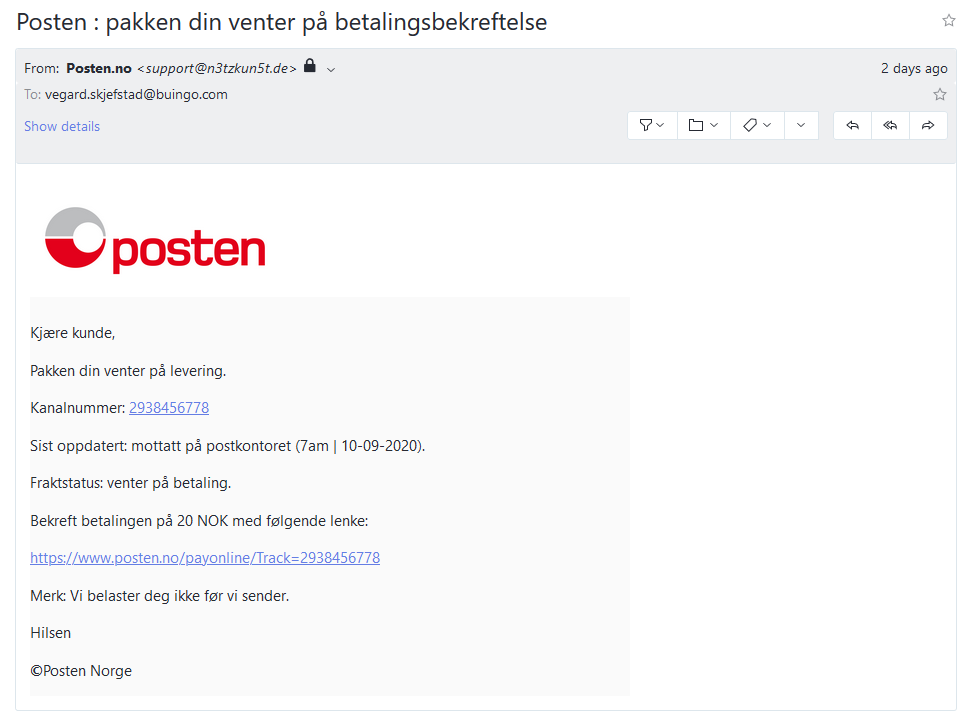
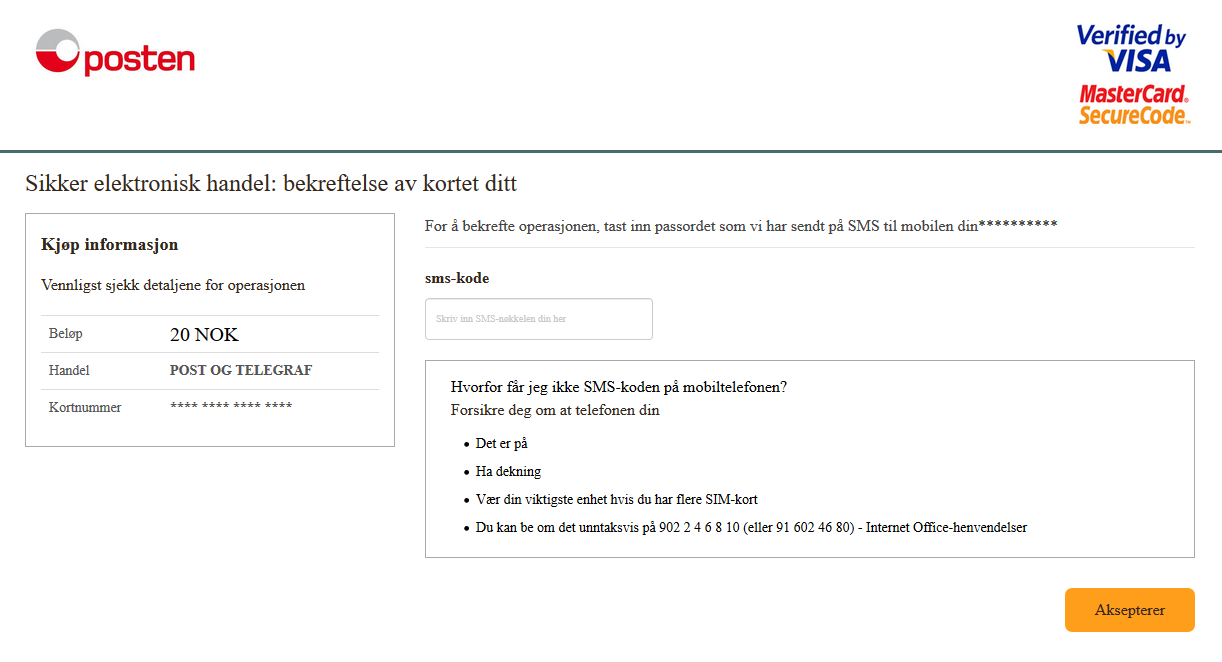
The e-mail I received, which you can see below, claim that Posten, the Norwegian postal office, is sitting on a package sent to me. To receive it, I have to pay a small charge of NOK 20, about $2/€2. A lot of people order stuff that is delivered by Posten, and while I’ve never heard of them demanding a surcharge like this, the amount is not outrageous.
Unlike the vast majority of scam e-mails, this particular one uses a Norwegian translation and grammar that isn’t terrible, which makes it look somewhat genuine. But there are still some telltale signs that reveal the illegitimate nature ot the e-mail:
- The senders e-mail address. The e-mail is not sent from the posten.no domain, which you’d expect, but from somewhere else entirely. The protocol used to send e-mails, SMTP, was created back in the days when everyone of the internet was friendly, and spoofing the sender’s e-mail address is therefore trivial. In recent years, however, mechanisms like SPF and DKIM have made it harder to spoof the sender’s e-mail address. Many e-mail servers will reject e-mails that fail SPF or DKIM validation, so in this case I guess the scammers have just assumed that most recipient won’t check the sender’s e-mail address. Some e-mail clients might even hide it from the recipient.
- The logo. While the logo is the correct Posten logo, it’s not served on the posten.no domain, but rather from a generic logo site.
- The word “kanalnummer”. Directly translated to English, this is “channel number”, which is not a word we’d associate with package delivery.
- The time and date format. Norway uses a 24 hour clock, so the “7am” time in the e-mail doesn’t make sense. Also, we use periods, not dashes, as date delimiter.
- The currency. To explicitly use NOK, Norwegian krone, as the currency looks weird when the e-mail is sent from a Norwegian company to a Norwegian recipient.
- The links. Hovering the mouse pointer over any of the links reveal that they won’t take you to the posten.no domain, which you’d expect. Instead, you’re sent to a suspicious looking .com-domain, which makes absolutely no sense. Some e-mail, particularly newsletters and similar e-mail, will contain link to weird URLs for tracking purposes. But an e-mail telling you to put money on the table usually won’t.
- The © symbol used in the signature. Have you ever seen this in any e-mail you’ve ever received from a company? Me neither.
As you can see, this e-mail, while it looks legitimate at first sight, contains a whole bunch of red flags. The sender’s e-mail address, and the site the links go to are the most obvious clues, and two things you should always check to confirm that an e-mail is legitimate or not.
But what happens to people who swallow the bait, and click on the links in the e-mail?
Through the Hoops
When a user clicks on any of the links in the e-mail, some scam countermeasures might kick in. I use Protonmail’s web based e-mail client, which displays the URL I click on, and asks me to confirm that I really want to go to the link. This clearly shows that I’m about to go to a web site that is not associated with the Norwegian postal service.
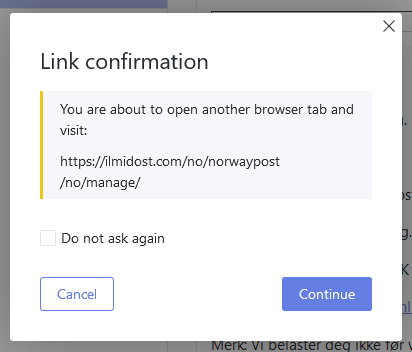
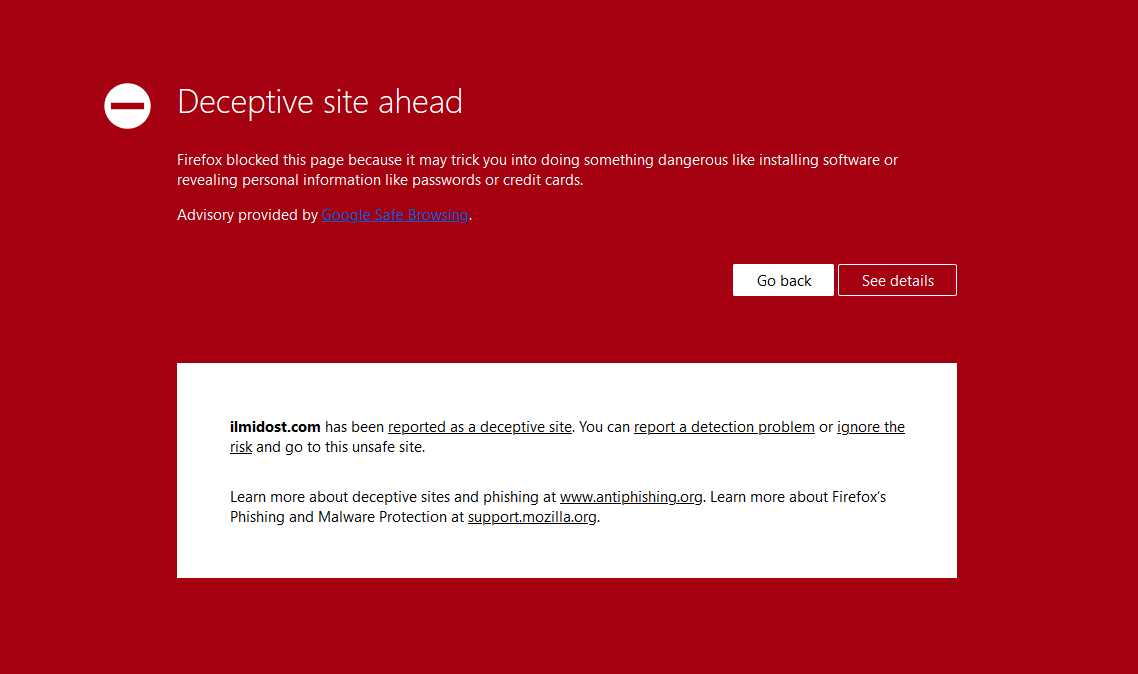
If I chose to go ahead and visit the site, Firefox displays a huge ass deceptive site warning. By default, Firefox blocks access to sites that have been reported using Google’s Safe Browsing1. It looks like the domain used for this particular scam has been reported already, and most internet users should be sufficiently warned that moving forward is a bad idea.
But the user might choose to ignore the browser’s very visual warning, and continue to the site anyway. It might also be that the user’s browser doesn’t support Safe Browsing, or that the site in some cases has not been reported yet.
Can I Haz Credit Card?
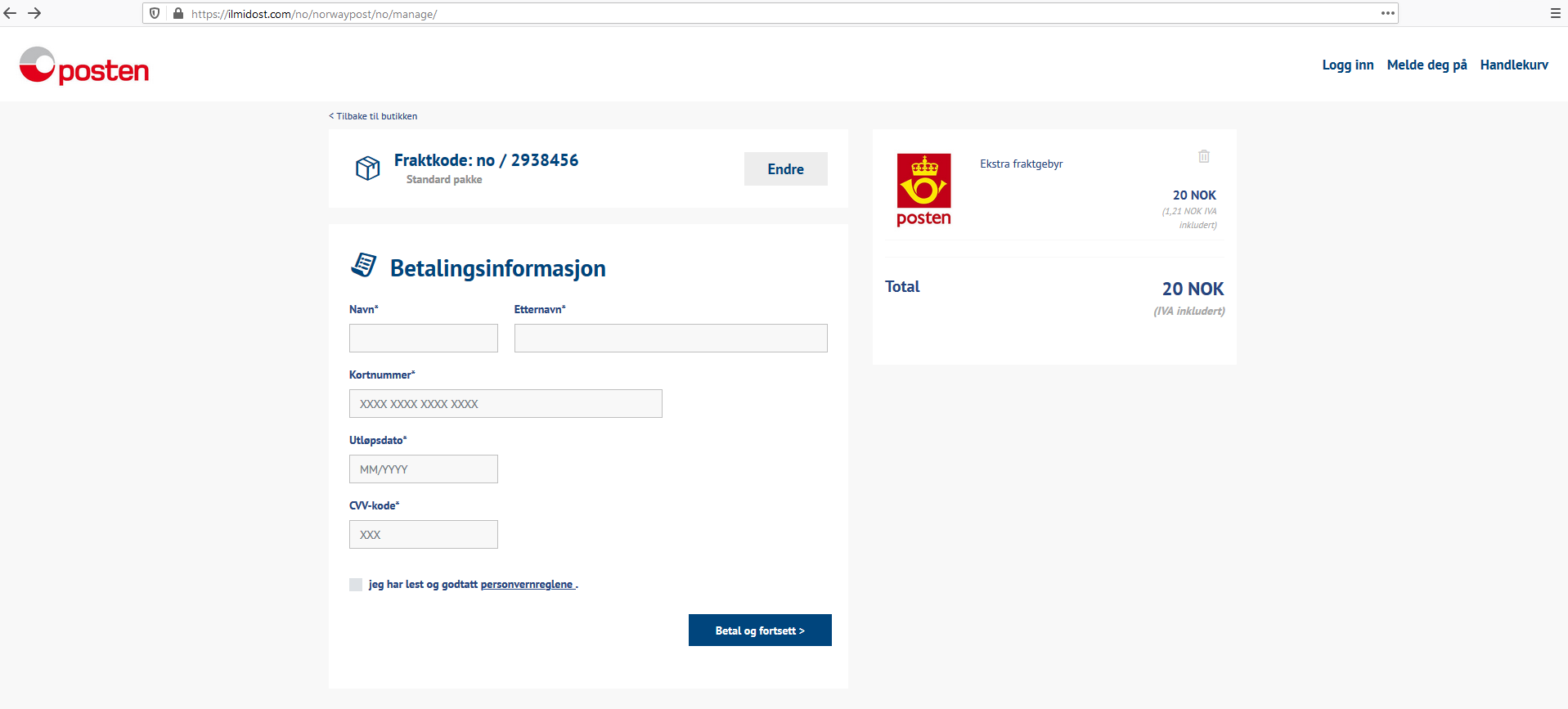
If the user eventually finds their way to the scammer’s site, they are greeted with the following:
This is the actual scam; collecting credit card information. This particular scamming technique is called phishing, which is “a fraudulent attempt to obtain sensitive information or data, such as usernames, passwords and credit card details, by disguising oneself as a trustworthy entity in an electronic communication”.
To get their package, the user has to pay the NOK 20, and they can do this by filling out this convenient form with their credit card information. Like the e-mail, the webpage also looks legitimate at first glance. But it also contains a lot of clues that something is amiss:
- The webpage’s address. The domain is clearly not associated with the Norwegian postal service’s main domain, which is posten.no.
- The “fraktkode” on the web page doesn’t match the “kanalnummer” value in the e-mail.
- None of the links on the page work, they all take the user back to the same page.
- The surcharge item in the “shopping basket” can apparently be removed, which is weird.
- The surcharge item in the “shopping basket” has a logo that Posten stopped using years ago.
- The 20 NOK surcharge apparently includes VAT, but the term “IVA” is used. In Norwegian, “MVA” is used. “IVA” is used in Spanish-speaking countries, which might give an indication of where the scam originates from.
- Some of the links on the page doesn’t make sense. “Tilbake til butikken” (“Return to the store”), “Meld deg på” (“Subscribe”), and “Handlekurv” (“Shopping Basket”), are not links you’d expect to find on a site belonging to the Norwegian postal service.
If the user, despite all the warnings, red flags, and clues we’ve seen so far, still decides to enter their credit card information in the form, the phishers get what they are after.
Please Wait, Scamming
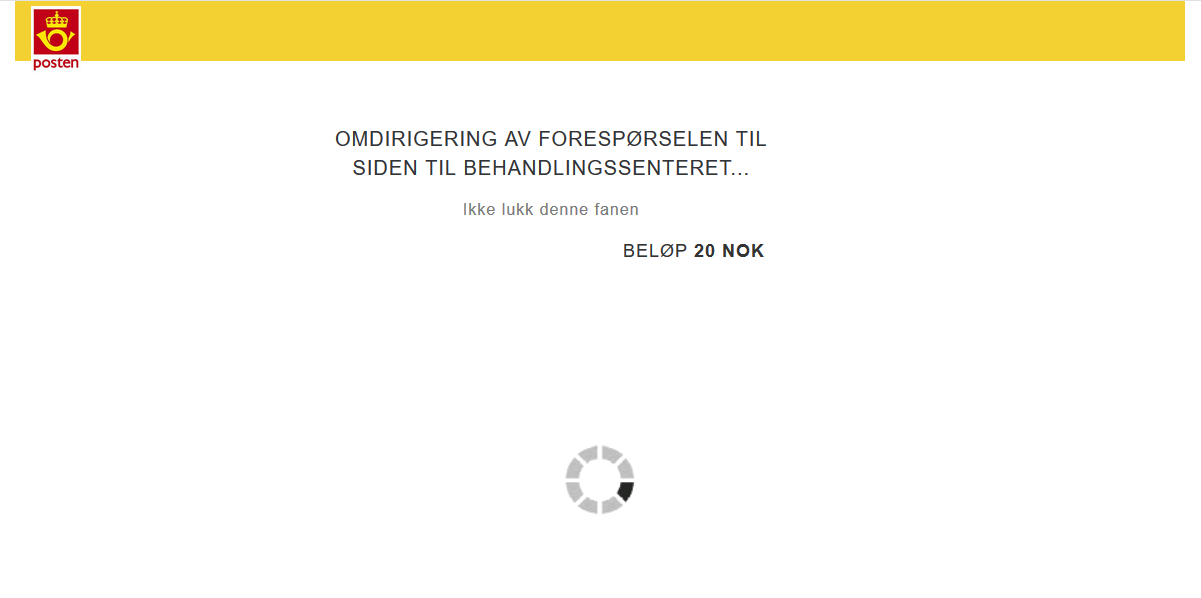
After submitting, the webpage sends the victim’s credit card information to a PHP script running on the server, and redirects the user to the page below.
This page use the same, very old logo that the surcharge item in the “shopping basket” on the previous page used. The language in the text is also a bit off. But all that doesn’t matter. The user has already sent their credit card information to the phishers.
If you’re reading this and your palms are getting sweaty because you’ve recently filled out the very forms you’re seeing here, then I recommend you call your bank and deactivate your credit card right now.
After 25 seconds, the user is redirected to the third, and final webpage involved in this scam. On this page, the user has to confirm their credit card details by entering a code that has supposedly been sent to the user’s cell phone number.
On this webpage, the phishers use the correct Posten logo, but everything else is just a long row of blaring klaxons. The user has not entered their phone number anywhere, and the Norwegian translation is way off everywhere. Clicking on the “Aksepterer”-button will just take the user back to the same webpage.
I’m not sure why the phishers thought this final page was necessary. Some sort of second factor authentication, like an SMS code, is often required to complete a credit card transaction, but at this point, the phishers have got what they wanted already.
Think, Then Click
As we’ve now seen, it’s not that hard to see that an e-mail isn’t what it pretends to be.
The three main indicators to look for are:
- Bad grammar, weird language and similar issues.
- The sender’s e-mail address doesn’t match what you’d expect judging by the contents of the e-mail.
- The links in the e-mail doesn’t take you to the site you’d expect judging by the contents of the e-mail.
If you’re not sure if you’re being phished or not, it’s better to stay on the safe side, and delete the e-mail. You can also contact the sender through their web page, customer support, or in similar ways to confirm that the e-mail is legitimate or not. But don’t contact the sender using contact details from the e-mail. Some phishers have even set up fake customer support lines.
So good night, and good luck.
A great effort by Google, but this is perhaps something that should not be controlled by a megacorporation. ↩︎
Feedback
This post has no feedback yet.
Do you have any thoughts you want to share? A question, maybe? Or is something in this post just plainly wrong? Then please send an e-mail to vegard at vegard dot net with your input. You can also use any of the other points of contact listed on the About page.
It looks like you're using Google's Chrome browser, which records everything you do on the internet. Personally identifiable and sensitive information about you is then sold to the highest bidder, making you a part of surveillance capitalism.
The Contra Chrome comic explains why this is bad, and why you should use another browser.